Associated Press (AP) has reported that Microsoft has linked an Iranian hackers group to an attempt to break into personal e‑mails accounts of the attendees of a high profile international security conference. According to the report, the group known as “Phosphorus” tried to hack attendees of the Munich Security Conference – a prominent annual conference which brings together international security policy decision-makers:
October 28, 2020 Microsoft says Iranian hackers have posed as conference organizers in Germany and Saudi Arabia in an attempt to break into the email accounts of “high-profile” people with spoofed invitations…The tech company said Wednesday it detected attempts by the hacking group it calls Phosphorus to trick former government officials, policy experts and academics..The targets included more than 100 prominent people invited by the hackers to the Munich Security Conference, which is attended by world leaders each February, and the upcoming Think 20 Summit, which begins later this week in Saudi Arabia but is online-only this year.
Read the rest here.
In October, the Global Influence Operations Report (GIOR) reported on cyber-attacks detected by Microsoft targeting the personal accounts of people associated with the Donald Trump Presidential campaign and which identified Phosphorus among the attackers. Further reporting on Iranian involvement in cyberattacks has included:
- A report on criminal charges raised against Iranian hackers, including the vandalism of US websites.
- A report on the latest DHS Homeland Threat Assessment that failed to identify Iranian efforts directed at the elections.
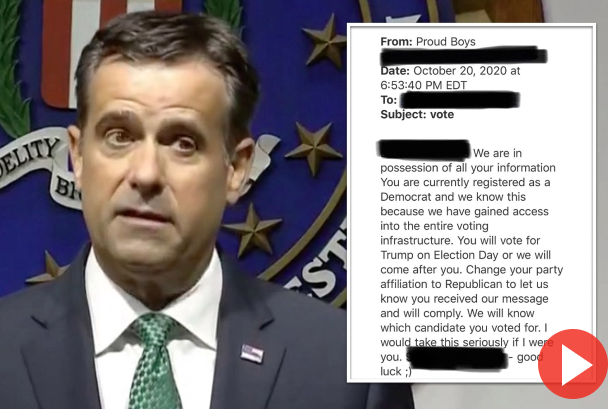
- A report that national security officials had accused Iran of trying to interfere with the upcoming US elections by sending voters fake emails intended to look like they had been sent by the Proud Boys, a far-right, pro-Trump group.
- A report that the US Department of Justice had seized 92 internet domains said to be used by Iran’s Revolutionary Guard as part of a global disinformation campaign.